ENSURE CONTINUOUS COMPLIANCE IN YOUR CLOUD

The term ‘compliance’ as it relates to cloud computing can elicit a wide variety of reactions. Some Developers cringe when they hear the word as they anticipate limited technology choices. Program Managers have images of project delays and increased complexity. Security and Compliance Officers see a framework for protecting the agency, its mission, and associated data (and maybe keeping their names off of the evening news).
Why is compliance so important for government agencies as they continue to adopt cloud computing? The answers are pretty straightforward. Most cloud security incidents today are due to some type of misconfiguration. Gartner predicted that ‘90% of the organizations that fail to control public cloud use will inappropriately share sensitive data and 99% of cloud security failures will be the customer’s fault.’ Whether it is an S3 bucket that has incorrect access settings or a misconfigured firewall, these incidents can be avoided through an effective approach to compliance.
In addition to security incidents, government agencies must comply with various laws and policies that dictate how information systems are to be managed. For example, in 2011 OMB released the Security Authorization of Information Systems in Cloud Computing Environments – also known as the FedRAMP Policy Memo – mandating that for all agency use of cloud services, FedRAMP be used for their risk assessments, security authorizations, and granting of ATOs. In addition, agencies must ensure applicable contracts require cloud service providers (CSPs) to comply with FedRAMP requirements. Additionally, if the government agency is also working with health data, then HIPPA security requirements must also be considered and followed.
The challenge that most organizations have with FedRAMP or HIPPA isn’t that they don’t understand the policies or controls. Rather, they don’t have a good understanding of which cloud services are actually FedRAMP authorized or HIPPA compliant. Not all services offered by a CSP have received a FedRAMP authorization, nor been certified as HIPPA compliant. An agency needs the ability to ensure projects and programs are only using services that have received proper authorization.
In addition to programs like FedRAMP, system integrators must contend with the Cybersecurity Maturity Model Certification (CMMC) that covers 17 capability domains, with 43 capabilities, and 171 practices across five different levels. For just CMMC Level 3, which is described as ‘Good Cyber Hygiene’, organizations must address 130 different practices, including all practices from NIST 800-171 r1.
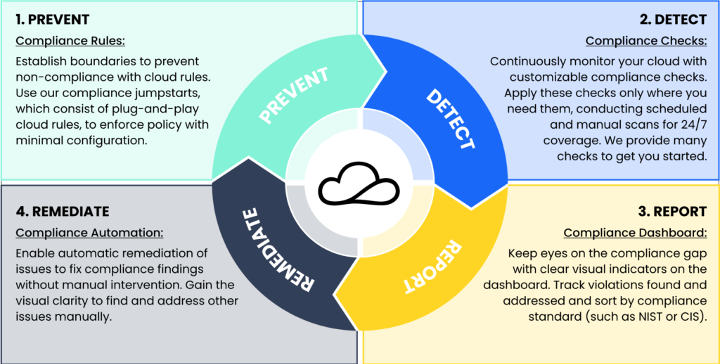
Organizations have historically used spreadsheets, checklists, and manual audits to track compliance. This process is time consuming and focused on finding things that occurred in the past. By the time something has happened it’s too late to do anything about it. Organizations need the ability to continuously prevent, detect, report, and remediate in real time.